Backblaze offers cost effective object storage solution that can be used to storage your files securely. Backblaze has two products, B2 and Personal Backup Backblaze Personal Backup offers unlimited backup storage to save all the files on one or more hard disk partitions on your Mac and PC. At the time of writing this article,…Continue reading Backblaze B2 + RClone for power users – automatically backup data to cloud – encrypted
How I reduced the docker image size by up to 70%?
One of the internal php projects that I manage, was using Ubuntu base for php/apache (Dockerfile available on Github) This weekend I have decided to convert this stack to Alpine+Nginx+PHP A quick google search shows that not many people are using this stack for their project. After a bit of research and testing, I published…Continue reading How I reduced the docker image size by up to 70%?
Azure AKS – Kubernetes Dashboard with RBAC Enabled
If you have recently deployed a kubernetes instance on Azure, you might have noticed that if you have selected RBAC enabled in your kubernetes cluster, the dashboard that comes preinstalled on the k8s cluster, has only the minimal permission. In order to have additional permission you would need to create a new cluster role bindings…Continue reading Azure AKS – Kubernetes Dashboard with RBAC Enabled
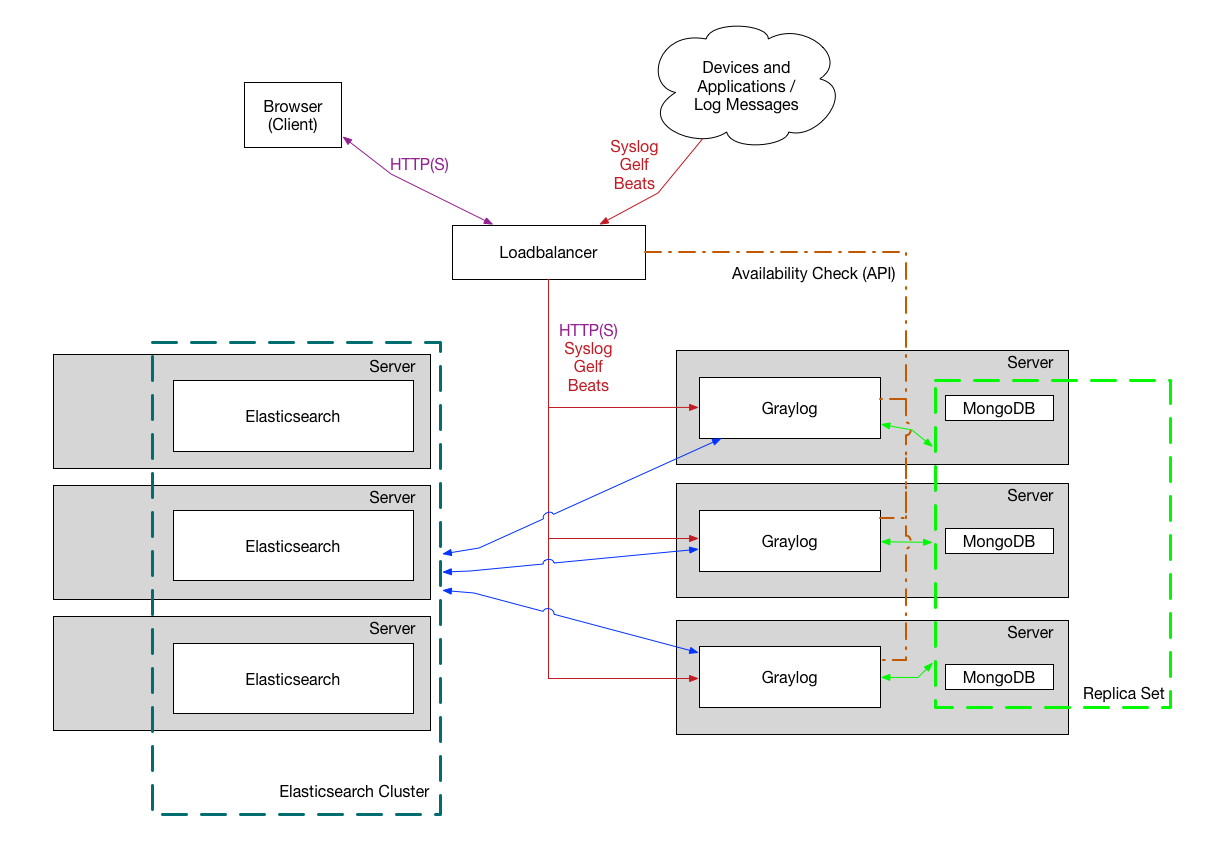
Setup scalable graylog on Azure Kubernetes (AKS) with Private IP and Nginx Ingress Controller
Recently I have been tasked with standing up a graylog cluster for our new development team. Even though I have stood up a highly scalable graylog on a regular IaaS/Virtual machine, utilizing Azure AKS was not something that I have done in the past. I was always skeptical about how would Azure handle the data…Continue reading Setup scalable graylog on Azure Kubernetes (AKS) with Private IP and Nginx Ingress Controller
Setup graylog locally on Windows/Linux/Mac
Here is the quickest way to deploy a development version of the Graylog instance locally on your desktop machine. Prerequisites Depending on your environment, you will have to install Docker Once installed, run these commands and you will have a fully working graylog running locally at http://127.0.0.1:9000/ Default username/password is admin/admin Expose additional ports By…Continue reading Setup graylog locally on Windows/Linux/Mac
Automatically update running docker container with the latest image
Watchtower is an open-source tool that scans the running container and restarts those containers with the same parameters if it detects a newer version in the repository. It supports public such as docker hub and private repositories such as Azure Container Repository or AWS ECR By default, Watchtower monitors all the container, but most of…Continue reading Automatically update running docker container with the latest image
Bash – Extract IP, Count Unique IPs and Sort
Given the apache access_log file content, to get the number of unique IPs use the following command
PHP code to check if a domain is enrolled in Incapsula WAF
Incapsula is a WAF service from Imperva. The company that I currently work for, is one of their biggest customers. We use Incapsula to protect our public websites. Recently I had an opportunity to work on developing a single page app that can show us the live status of the domain enrollment so that we…Continue reading PHP code to check if a domain is enrolled in Incapsula WAF
Extend osDisk partition on Azure Linux CentOS 7.x VM
Azure VMs usually comes with the default osDisk 30-50GB and often you will find that needs to be increased. The following steps can be used to extend the disk as well as the partition. Assumptions Here we assume that the VM is on CentOS 7.x version. (The same steps should work for lower version as…Continue reading Extend osDisk partition on Azure Linux CentOS 7.x VM
Automated MongoDB backup on Docker Swarm and save on AWS S3
AWS doesn’t have a PaaS service offering for MongoDB at the moment. So it is the DevOps’s responsibility to maintain their own backups of the production MongoDB databases. So I’ve developed a custom script that makes use of Docker containers to deploy a backup container. This script will generate backup in specified intervals and upload…Continue reading Automated MongoDB backup on Docker Swarm and save on AWS S3